|
|
 |
Read Chapter 15 in your text and this lesson. Then, complete hw 15. Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). Transport protocols are responsible for opening connections when required, sending acknowledgments, defining the destination services that should handle their segments and notifying the receiver what service sent this segment. You may have noticed that I am not calling the data unit at layer four a packet. Packet is specifically a layer three term. At layer four we'll use the term segment. Terms used to specify the protocol data
While IP supports many protocols at layer four, UDP and TCP are the main protocols. UDP offers an unreliable, yet very simple connectionless service to the highest layers of the Internet Model. On the other hand, TCP offers a reliable connection-oriented service. Together these two protocols carry most of the communications across the Internet. TCP would be a good choice for file transfers that require accuracy. You copy a file once and you expect every bit to arrive error free. If a single bit is in error, the whole document might be corrupted. In comparison, UDP would be a good choice for streaming updates, such as voice or video. For voice, we would need to send 8000 packets per second with an 8-bit voice sample in each. That would provide fairly high quality. If a single packet is lost, we won't even know. So there would be no value in stopping everything and waiting for a lost packet to be retransmitted. Ah, this brings up some important issues between UDP and TCP. UDP has no flow control or error control which means that the header is very small. UDP provides low overhead compared to TCP. TCP uses sliding window flow control over a logical connection to the distant peer. Flow control and error control messages are sent and through this mechanism, the exact duplication of a transferred file is ensured. Finally, time sensitive protocols tend to use UDP because there is no value in requesting retransmissions. They take too long. If a packet is missing, the layer will go on to the next packet. No time to delay, just deliver what you have and go on. Example: UDP would be used to support communications for on-line games, like tank battles or airplane dueling. At regular intervals, your game client software sends out a position update, noting your exact location in the game world, the velocity you are moving at and the direction you are traveling (position, speed, and heading). All this can be updated in a relatively small packet, say 60 times a second. Perhaps 30 of these position updates are enough to simulate smooth movement on the screen. That means some of these can be lost in transit without affecting the game quality. When a packet is lost, the client software simply waits for the next packet to update the position on the screen. Loss of many packets will result in jerky motion in the game. User Datagram Protocol, UDP
Source Port is the port number of the service above UDP that sent this segment. Because multiple services might be using UDP at the same time, such as DNS and Simple Network Management Protocol (SNMP), the services are assigned port numbers that are unique. This field is optional and when not used the field is filled with zeros. Destination Port is the port number of the service that will receive this packet upon is arrival at the destination. UDP hands the segment up to the service (which resides at layer 5). Ports range from 1 to 65,536 with the lowest several 100 port numbers assigned for specific services. For example, both TCP and UDP have assigned port 53. Length is the total number of octets including both the header and the data field. If there is no data, the length would be eight, the minimum. With sixteen bits, the maximum length of a UDP data unit is 65,536 octets. Checksum is an error check on both the header and the data. This field is optional. If not used, the field is set to zero. The purpose of UDP is to add the destination port number and the option of an error check to the data encapsulated in an IP datagram. Remember that IP checks for errors in the header only. Some services that take advantage of UDP and their assigned port numbers.
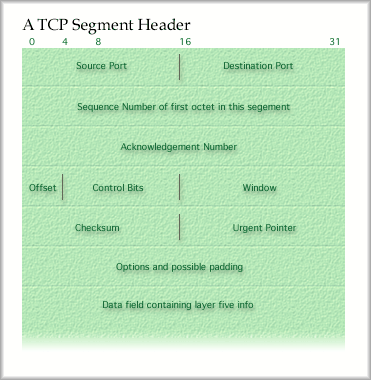
Transmission Control Protocol, TCP * flow control through a modified sliding window protocol An important note here is that TCP uses a special kind of sliding window for flow control. Each TCP segment sent includes a window field. The field has value that indicates how many octets the receiver is ready to receive (not the number of segments to send). This is the credit scheme that Stallings discusses in Chapter 17. It is done to directly notify the sender how much buffer space the receiver has left. Take a look at the TCP segment header below.
Like the UDP header, there is a Source Port and a Destination Port. These define the sending service and the receiving service (at layer five). For example your web browser would make requests to a Destination Port of 80 on a web server. The IP hands the datagram up to the TCP layer. TCP checks for errors, then strips the header off. Finally, it hands the data field off to the appropriate service, a web server service on Port 80 in this case. Some common TCP port numbers:
Segmented data requires numbers on each segment so that they may be reassembled. IP datagrams can only be 65,536 octets, including header, so it would be wise to make the TCP segments no larger than about 65,516 octets. The numbered segments are marked in the Sequence field. The octets in the original file are numbered. The number of the first octet to appear in this segment is placed in the sequence field. Acknowledgment Number contains the sequence number of the octet expected to appear first in the next segment. This is your garden variety ACK. Offset, just like the IHL in IP, holds a value for the number of 32-bit words in the header. The Control Bits, some of which are reserved bits, provide special functions to the TCP connection. For instance, bits in this field can be set to force the connection to be reset, to notify the receiver that urgent data is included that must be read immediately or to indicate that the last segment has arrived. The Window field implements the credit scheme mentioned earlier in this lesson. The number or octets that the receiver is willing to accept are placed here. This is how flow control is imposed on the sender. The value of the Checksum field allows for error checking of both the header and the data field. At times, the sender or receiver would like to send an urgent message (a control message) to the other end. This might be a notice that the user closed their browser window and the connection should be closed immediately, or that the receiver has no more buffer space and the sender should stop until further notice. An Urgent Pointer field holds the sequence number of the first octet AFTER the urgent data. That allows the TCP process to determine how far to read to get all the urgent data. Usually this field just hold zeros. If the options field is included it indicates to the opposite end the maximum size segment that it may send. The minimum size of a TCP segment header is 20 0ctets. The header must always be padded so that it ends on a 32-bit word boundary. If necessary padding is used to fill in the options field, though no additional options have been specified at this time. So, TCP chops a file up into 65,000 octet segments, makes a note of the sequence numbers of the octets of that file and then sends out those segments when given permission by the receiver. Please note that sliding window is implemented for both directions of a TCP connection. TCP is a connection oriented service. A setup message is sent, acknowledged and sequence number counters are synchronized. It turns out that that TCP standard specifies that sequence numbers run consecutively for multiple TCP connections. The TCP doesn't roll over its counter at the end of a window. The sequence numbers just keep rising, until they reach the maximum of 232, or about 4.3 billion. In combination, TCP and IP provide a method for data to flow as independent packets across interconnected networks reliably and through a virtual circuit. Why a virtual circuit, you ask? TCP is responsible for reordering packets and reassembling them before handing them up to layer five services. To the upper layers the information appears to arrive in order. |
||||||||||||||||||||||||||||||||||||||
| [INF 680 Syllabus] [How to Start] [Schedule] |
Used with permission of the Author; Copyright (C) Kevin A. Shaffer 1998 - 2022, all rights reserved. |